Information Security & Management
Home»Corporate Governance»Risk Management»Information Security & Management
Information Security & Management
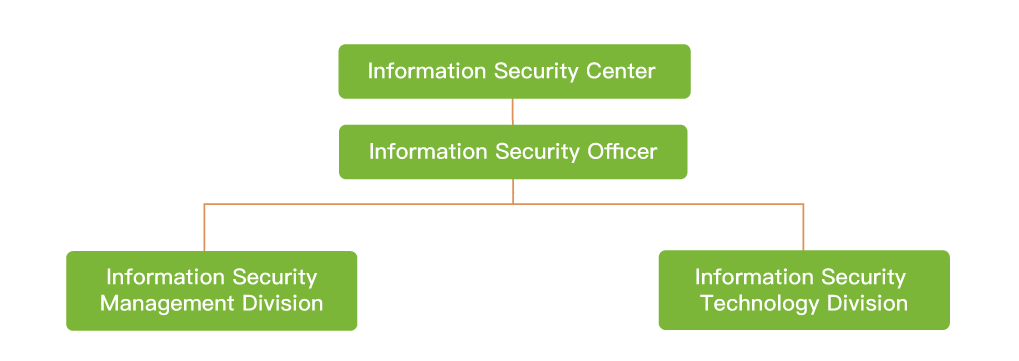 The Company’s Board of Directors has resolved to establish a designated information security unit and appoint Information Security Officer in Q1 2022. The designated information security unit is named the “Information Security Center,” which reports directly to the CEO or his designated representative, and is responsible for convening the PIS (Proprietary Information Security Committee) meetings, promoting important cybersecurity policies and plans, while continuously improving and strengthening various protective measures. The “Information Security Center” consists of the “Information Security Management Division” and the “Information Security Technology Division”. The Information Security Center regularly reports relevant risks, issues and effectiveness of management. The Committee would report to the board of directors at least once every year on the progress of information security implementation and the latest reporting date was on December 27, 2024.
Information security policy, concrete management programs and resources invested in information security management:
The Company values the importance of information security maintenance. We have established "Information Security Management Policy" and "Information Security Risk Management Framework" in 2009. We initiated plans to obtain ISO27001 certification since 2020, and proactively promote the implementation of information security measures in 2021. We have successfully obtained the certification in Q2 2022, completed ISO 27001:2022 transition version and expanded scope of certification coverage by 2.5 times with all information systems included. Current certificate is valid from May 4, 2022 to May 4, 2025 (for details on our ISO certificates, please refer to https://www.quantatw.com/Quanta/english/corporategovernance/certificates.aspx).
The Company is devoted into expanding the scope of certification through the implementation of information security management system to con-currently protect the Company and customers. We will further strengthen our capabilities in information security incidents response to meet the rising information security needs.
Quanta has invested in information security insurance from internationally known insurance companies since 2008. Specifically, the Company has increased the insurance premium in response to rising awareness of information security issues and stakeholders’ expectation. We have increased coverage by purchasing supplemental insurance on Social Engineering and Network Interruption-System Failure, to transfer and diversify contingent risks. Moreover, considering the difficulty of implementing boarder information security control, we have further extended the insurance coverage to include all major operation sites around the world. Planning of relevant insurance amount and insurees is based on the Company’s financial status and actual needs.
In the most recent fiscal year, the Company did not incur any losses due to major information security incidents. Major operations is highlighted below, please refer to the Company’s website and the “Information Security Management” section under the “Sustainable Governance and Ethics” chapter of the Company’s annual ESG report for details:https://www.quantatw.com/Quanta/english/corporategovernance/riskmanagement.aspx
https://www.quantatw.com/Quanta/english/esg/ESG2023/Quanta_ESG_EN_2023.pdf
The Company’s Board of Directors has resolved to establish a designated information security unit and appoint Information Security Officer in Q1 2022. The designated information security unit is named the “Information Security Center,” which reports directly to the CEO or his designated representative, and is responsible for convening the PIS (Proprietary Information Security Committee) meetings, promoting important cybersecurity policies and plans, while continuously improving and strengthening various protective measures. The “Information Security Center” consists of the “Information Security Management Division” and the “Information Security Technology Division”. The Information Security Center regularly reports relevant risks, issues and effectiveness of management. The Committee would report to the board of directors at least once every year on the progress of information security implementation and the latest reporting date was on December 27, 2024.
Information security policy, concrete management programs and resources invested in information security management:
The Company values the importance of information security maintenance. We have established "Information Security Management Policy" and "Information Security Risk Management Framework" in 2009. We initiated plans to obtain ISO27001 certification since 2020, and proactively promote the implementation of information security measures in 2021. We have successfully obtained the certification in Q2 2022, completed ISO 27001:2022 transition version and expanded scope of certification coverage by 2.5 times with all information systems included. Current certificate is valid from May 4, 2022 to May 4, 2025 (for details on our ISO certificates, please refer to https://www.quantatw.com/Quanta/english/corporategovernance/certificates.aspx).
The Company is devoted into expanding the scope of certification through the implementation of information security management system to con-currently protect the Company and customers. We will further strengthen our capabilities in information security incidents response to meet the rising information security needs.
Quanta has invested in information security insurance from internationally known insurance companies since 2008. Specifically, the Company has increased the insurance premium in response to rising awareness of information security issues and stakeholders’ expectation. We have increased coverage by purchasing supplemental insurance on Social Engineering and Network Interruption-System Failure, to transfer and diversify contingent risks. Moreover, considering the difficulty of implementing boarder information security control, we have further extended the insurance coverage to include all major operation sites around the world. Planning of relevant insurance amount and insurees is based on the Company’s financial status and actual needs.
In the most recent fiscal year, the Company did not incur any losses due to major information security incidents. Major operations is highlighted below, please refer to the Company’s website and the “Information Security Management” section under the “Sustainable Governance and Ethics” chapter of the Company’s annual ESG report for details:https://www.quantatw.com/Quanta/english/corporategovernance/riskmanagement.aspx
https://www.quantatw.com/Quanta/english/esg/ESG2023/Quanta_ESG_EN_2023.pdf
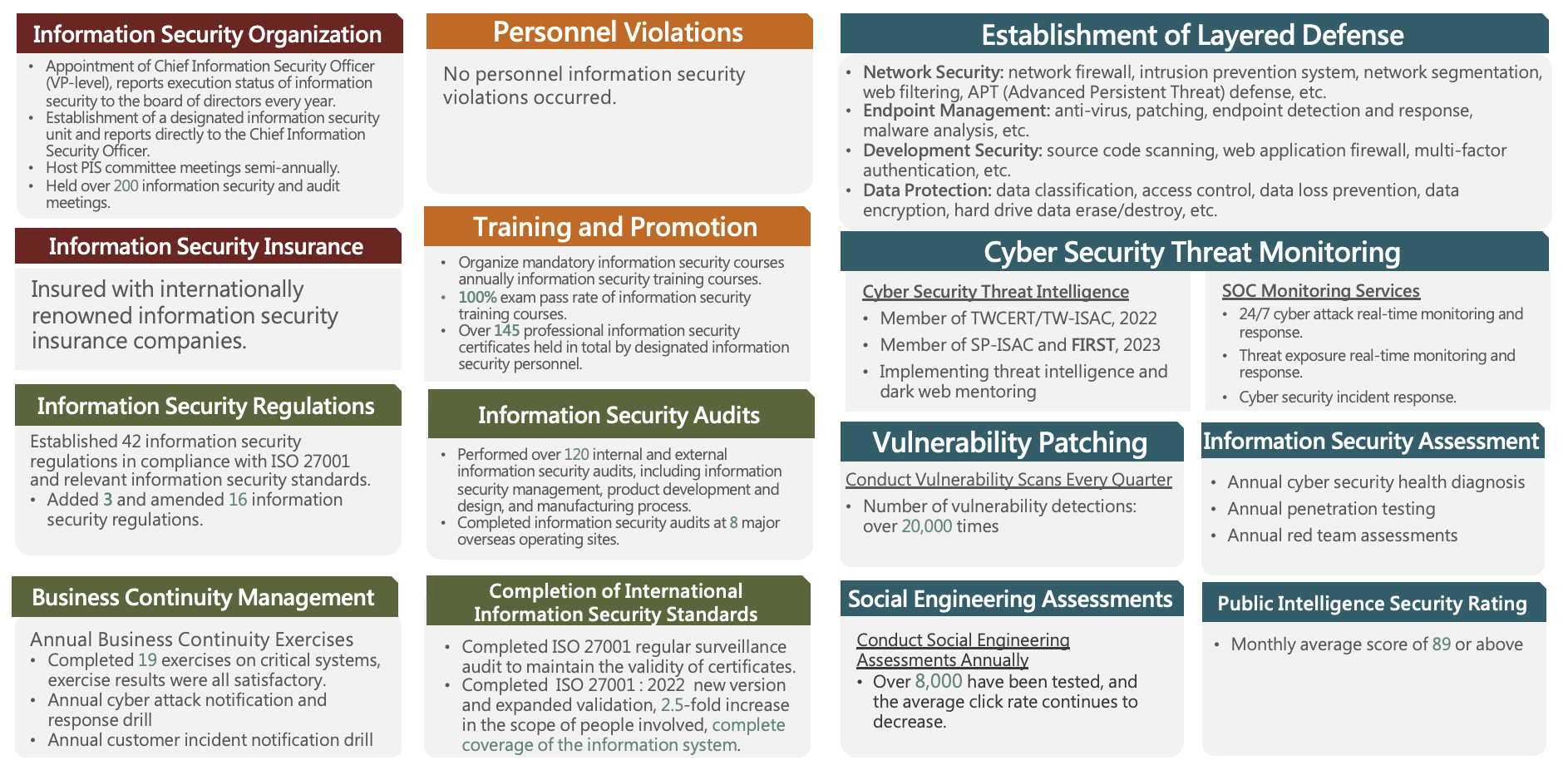 The boundary of technological development is unlimited, and it deepens our reliance on networks and other information tools. As a result, information security has become a focal point, as even minor vulnerabilities can disrupt normal business operations. The company fully understands the urgency of keeping cybersecurity mechanisms up to date in order to respond promptly to the ever-evolving cyberattacks. In addition to actively joining both domestic and international cybersecurity response organizations to stay informed about the latest threat intelligence and various cybersecurity investigation techniques, we continuously strengthening our cybersecurity depth and optimizing protective measures. We are promoting a zero-trust architecture and utilizing cybersecurity AI technology to enhance the strength of our security defenses and provide comprehensive cybersecurity monitoring. We rigorously assess risks and controls, allocate cybersecurity budgets annually, and strengthen information and communication technology security defenses.
Regarding the handling of cybersecurity incidents, the Company has implemented an incident response procedure, established an incident management process plan, and we also perform annual cybersecurity incident reporting drills to implement the reporting of cybersecurity incidents. We regularly perform self-assessments based on the " Guideline of Cyber Security Management for TWSE/TPEx Listed Companies." Additionally, internal and external cybersecurity audits are carried out at each operational site, as well as client audits, with no significant deficiencies found. For both internal and external cybersecurity threats, we have implemented specific cybersecurity solutions to protect against and manage risks effectively.
The boundary of technological development is unlimited, and it deepens our reliance on networks and other information tools. As a result, information security has become a focal point, as even minor vulnerabilities can disrupt normal business operations. The company fully understands the urgency of keeping cybersecurity mechanisms up to date in order to respond promptly to the ever-evolving cyberattacks. In addition to actively joining both domestic and international cybersecurity response organizations to stay informed about the latest threat intelligence and various cybersecurity investigation techniques, we continuously strengthening our cybersecurity depth and optimizing protective measures. We are promoting a zero-trust architecture and utilizing cybersecurity AI technology to enhance the strength of our security defenses and provide comprehensive cybersecurity monitoring. We rigorously assess risks and controls, allocate cybersecurity budgets annually, and strengthen information and communication technology security defenses.
Regarding the handling of cybersecurity incidents, the Company has implemented an incident response procedure, established an incident management process plan, and we also perform annual cybersecurity incident reporting drills to implement the reporting of cybersecurity incidents. We regularly perform self-assessments based on the " Guideline of Cyber Security Management for TWSE/TPEx Listed Companies." Additionally, internal and external cybersecurity audits are carried out at each operational site, as well as client audits, with no significant deficiencies found. For both internal and external cybersecurity threats, we have implemented specific cybersecurity solutions to protect against and manage risks effectively.




